There are several key steps a transaction must go through before it is added to the blockchain. There is authentication using cryptographic keys, authorisation via proof of work, the role of mining, and the more recent adoption of proof of stake protocols in later blockchain networks.
TL;DR : TOO LATE, DIDN'T READ
A Transaction is requested and broadcasted from the node which is send the transaction and the transaction gets picked up by various miners. Each miners than runs some computation on the transaction to validate and verify.
Once the transaction is validated, it is then added to a block with other transactions and the block created by the group of transactions is added to the Blockchain.
What role do miners have in Blockchain Ecosystem?
Miners are very essential and integral part of the Blockchain Ecosystem. Miners ensure that the network is fair, safe, and secure by validating and approving the transactions. Miners validate the transactions broadcasted by the nodes in the network.
Once the transactions are approved and validated by the miners, the transactions are then confirmed. Thereby, miners allows the the recipients to receive the cryptocurrencies sent to them by the initiators of the transactions.
Miners use special kind of software to solve mathematical puzzles/problems and are rewarded newly created coins along with the transaction fees(gas fees) paid by the sender.
This gives a good use to issue new currency and create an incentive for more users(nodes) to become miners. Miners have to provide solutions to complex mathematical problems according to the Consensus Algorithms specific to the network.
Each Blockchain Transaction requires 4 features/steps to complete:
They are -
- Cryptographic Algorithm.
- Decentralized Network.
- Consensus Algorithms.
- Distributed Ledger.
Cryptographic Algorithm:
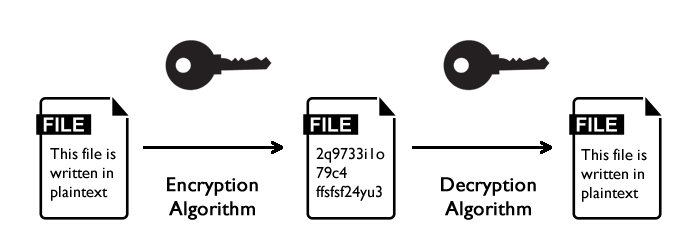
It is an algorithm used to encrypt data by altering the data from readable plain text format to non-readable cipher text and back.
What are Cryptographic Algorithms? AND How does it Work in Blockchain Technology?
Cryptography is an algorithm which is used to convert data from readable format to cipher text and back to readable format. We use cryptography algorithms on daily basis without even knowing. Well-known messaging apps use cryptography to encrypt data. There are 2 kinds of cryptography algorithms i.e.
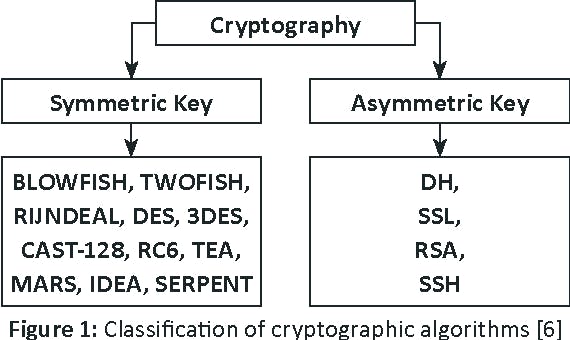
- Asymmetric Key Cryptography and
- Symmetric Key Cryptography
Asymmetric Key Cryptography
Asymmetric Key Cryptography uses 2 types of keys i.e.
- Public key which is used for Encryption and
- Private key which is used for Decryption.
Symmetric Key Cryptography
Symmetric Key Cryptography uses one and only single secret key for both Encryption and Decryption.
EXAMPLE of how its all done -
For Cryptography example in existing blockchains, Bitcoin uses Asymmetric Key Cryptography to leverage the public key and private key to create Digital signatures of the users to initiate the transactions which are eventually broadcasted through the network.
These Digital Signatures provide authentication and validation to the transaction. It ensures the integrity of the data.
These Digital Signatures uses used by taking the infromation to be transmitted and running a hash algorithm to generated 32-64 bit hash value which is then encrypted using the public key which results in a Digitally Signed Document.
Once the Receiver get the digitally signed document, he/she decrypts the document using the Signer's Public Key. The hash value generated after decryption is compared to another hash value which is locally generated by the verifier using the algorithm used by the signer.
If the hash values are equal, the signature is considered valid and the verifier then can access the document/information.
Decentralized Network
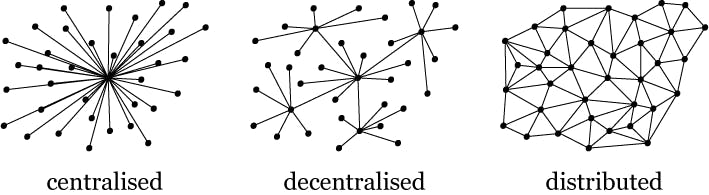
Decentralized Network is the network where every node in the network has the copy of data. It eliminates the need of trusting any single entity.
By definition, A Decentralized Network is a system where Miners play important roles in validating the transactions in process. Now, let us discuss this in detail.
There are 2 types of Networks:
- Decentralised Network &
- Centralized Network
Blockchain is made on Decentralized Network which can be identified by P2P(peer-to-peer) connections of miners playing essential roles in validating every transaction.
This eliminates the need of Central Entities/Authorities to rule the network where here in the Decentralized Networks, the control is in the hands of Individual User. Decentralized Netwroks ensures that everything works Fairly and Securely.
The Centralized Networks can be identified by a compulsory Centralized point which can be a Client Software or Hardware through which all the information that is on the network must be passed.
Consensus Algorithm
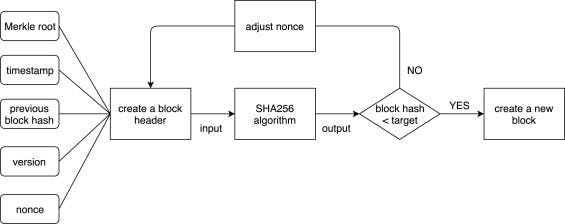
It is an Algorithm or we can say a Mechanism due to which the network consisting of many nodes agrees on a single data value or simply, be in Sync.
By Definition, A Consensus Algorithm is a concept of computer science which is used to reach an agreement on a single data value or a single state of network when a system is distributed. So, Consensus Algorithms provide reliability in a network,or in other words, We can say Consensus Algorithms are the set of rules that keeps the network in order.
- It ensures that all the transactions taking place on the network are genuine and all the nodes agree on the consensus of the ledger.
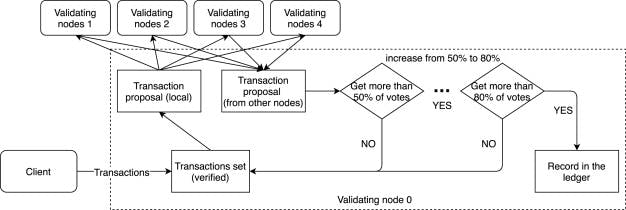
Features of Consensus
EFFICIENCY offered by the consensus protocol is very good. Consensus protocols makes the transactions of the exchanges quicker and simpler as no third party is required.
SECURITY is another key feature of the consensus protocol that ensures not having a single point of failure. For a hacker, to hack blockchain, he/she might need to hack countless numbers of nodes on the network at the same time to collect very small pieces of data and put them together. which is neither practically possible nor beneficial in terms of ROI(Returns on Investment). Moreover, it is very resilient too because due to Decentralization, even if a a device fails, the information continues to exist securely somewhere else.
REAL-TIME TRANSACTIONS is also a key feature of the consensus protocols because it enables really fast and secure transactions as oppose to any other central third parties.
There are different consensus algorithms, such as
- Proof of Work
- Proof of Stake
- Proof of Elapsed Time (PoET)
- Pratical Byzantine Fault Tolerance (pBFT)
Proof of Work
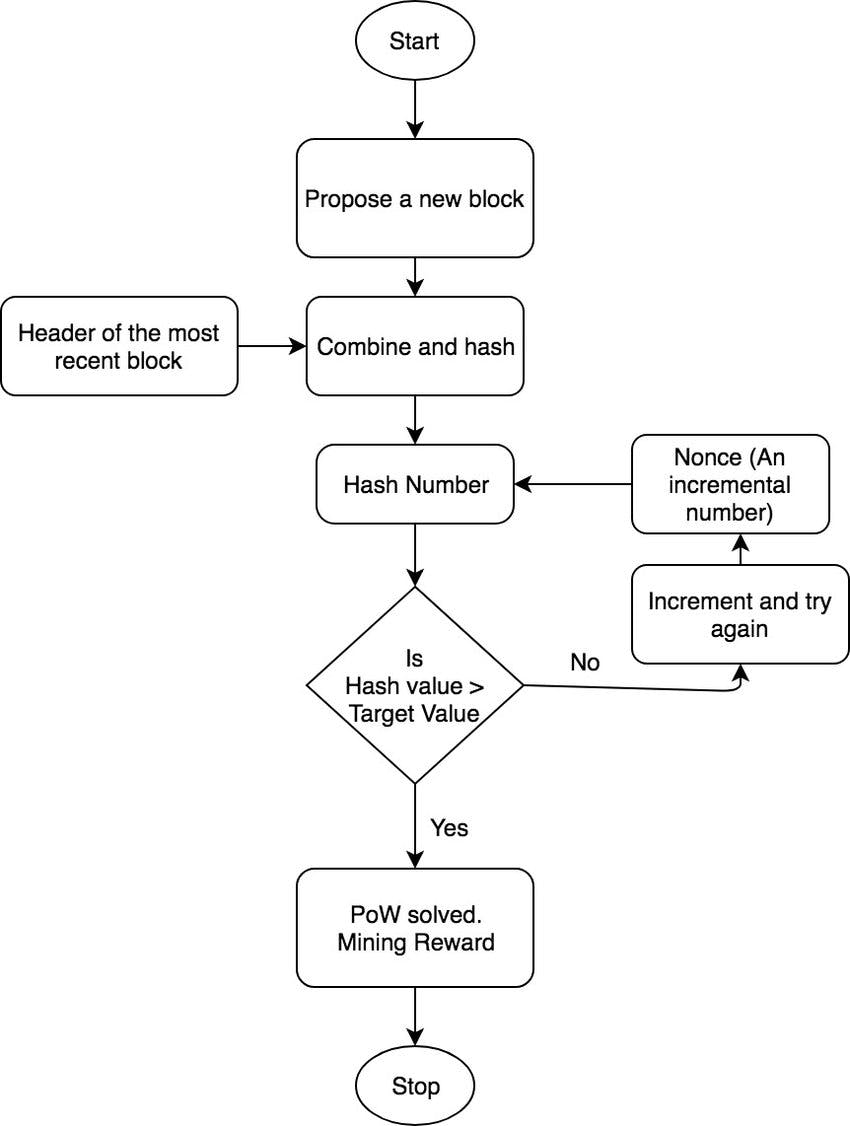
Proof of Work is a consensus algorithm in the blockchain network which which is used to confirm transactions with the help of mathematical puzzles and produces a new block. Proof of work requires nodes to do some work in order to participate. Work which is easily verifiable by the network but difficult to do for the miner node. In the Bitcoin Blockchain, Proof-of-Work works such as miners compete to solve a block which contains some of the verified transactions and have that solved block accept to be added to the Global Blockchain Network. The only way to get this solved Block accepted to be added to the Network is by guessing a special number/value in a certain amount of mining. If a miner node is not able to solve this special value, it must start over with solving another block and guessing the special value that solves the puzzle for that other block.
Proof-of- Work comprises of 3 main characteristics
- The Nonce
- The Hash Code
- The Transaction
The Nonce
( abbreviation for "Number used once"). It is just like OTP for taxi apps, you can't start the ride without the OTP. Similarly, Nonce is important for the miner to get the solved block accepted. It is a random number whose value is set so that hash of the block will contain a leading zeros. Thus, it is the number miners are solving for.
The Hash Code
Hash Code is basically a numeric value that is used to compare to identify an object at the time of quality testing. It serves as an index for an object. The main purpose of hashcode is to help with efficient lookup and insertion in data collections that are subject to chance on a hash table. Basically, the code generated by taking an input and converting to cryptographic output using a mathematical algorithm is what we call 'hash code'. Hashing is a algorithm to convert a sequence of characters into a string of 64 letters or numbers.
The transaction
Miners have a block of transactions to solve and they want to be a first one to do so in order to get the mining rewards. Every miner knows the hash of the previous block as it is a public information. So, a miner begins with the previous block hash to start creating a new block.
Some Popular coins like Bitcoin, Ethereum 1.0, Litecoin, and Dogecoin uses Proof-of-Work.
As every Consensus Algorithm, Proof-of-Work has its own pros and cons:
PROs
- High Level of Security
- Provides a Decentralized Method of Verifying Transactions
- Allows Miners to earn Crypto Rewards
CONs
- Inefficient with slow transaction speeds
- Expensive Fees
- High Energy Usage
- Mining often requires powerful and expensive equipment
Proof-of-Stake
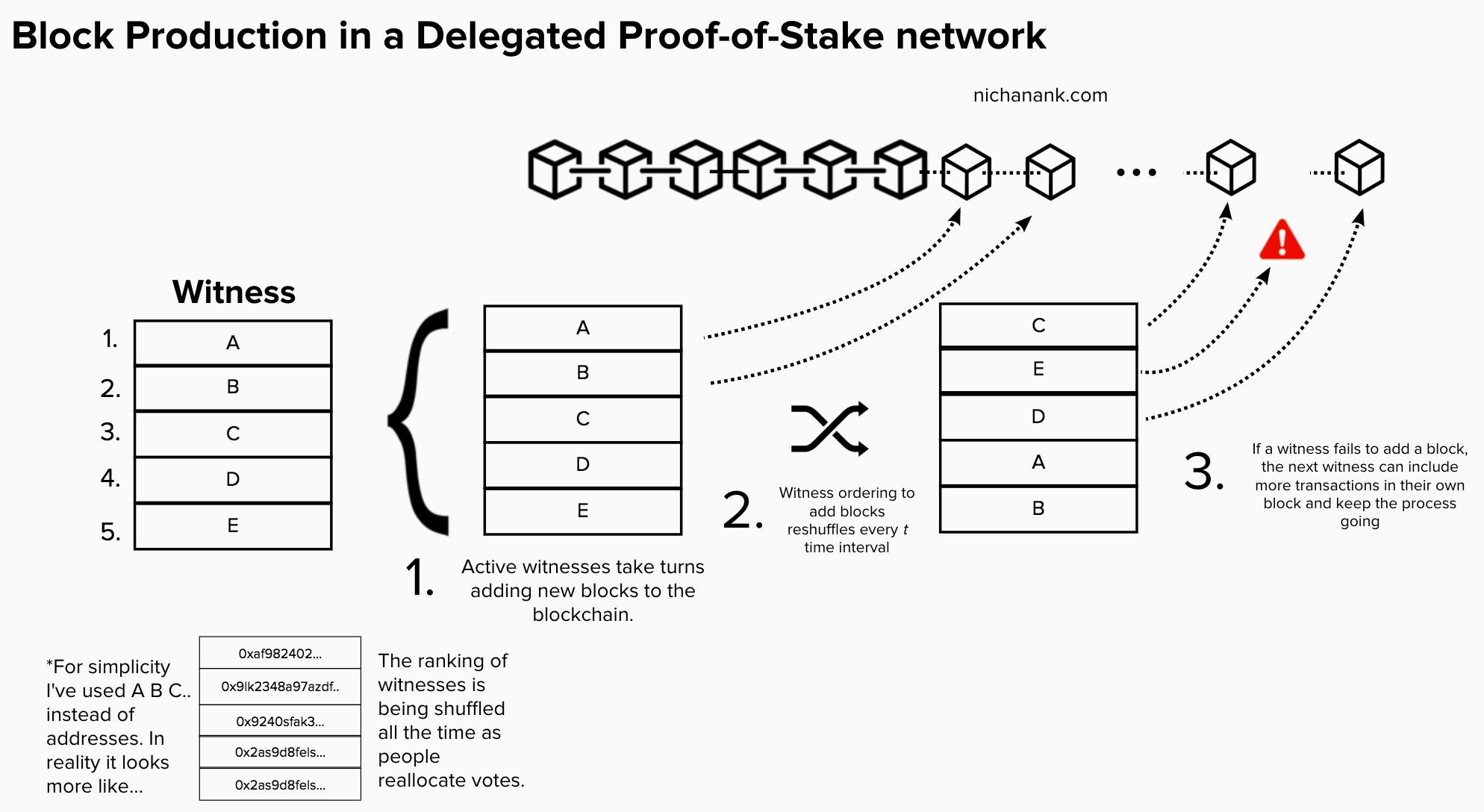
Proof-of-Stake is a low cost, low energy consumption consensus algorithm which states that a person can mine and validate transaction based on how many coins do they hold/stake.
In Proof-of-Stake,
Anyone who holds the base cryptocurrency can become a validator, although sometimes a deposit to be locked-up is required.
A validator's chance of mining a block is based on how much cryptocurrency they have staked. For example, if you owned 1% of cryptocurrency, you will be able to mine 1% of all transactions
The Proof-of-Stake(PoS) protocol will randomly choose the give the right to create a block among the selected validators absed on the value of their stakes. The chosen validator is rewarded with a part or the whole part of the transaction fees.
Like every Consensus Algorithm, PoS has it's own pros and cons.
PROs
- Energy Efficient
- Fast Transactions
- Inexpensive Transaction Processing
CONs
- Not proven in terms of security as compared to PoW
- Validators with large holdings can have excessive influence on transaction verification.
Proof of Elapsed Time
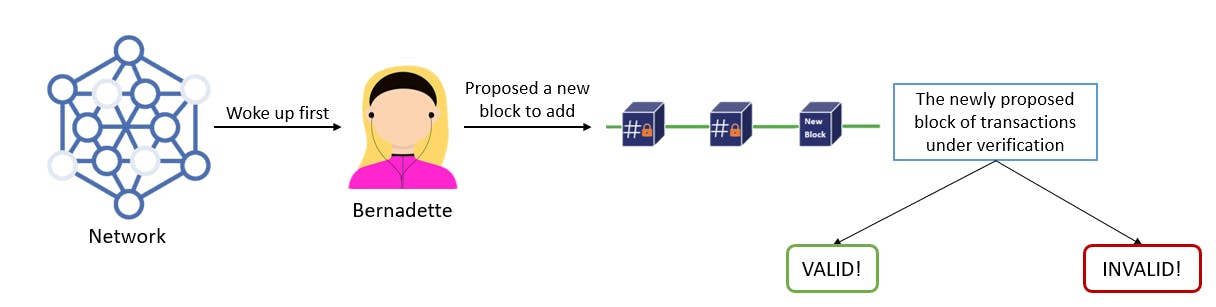
Proof of Elapsed Time is a Consensus Algorithm which prevents two main problems that current mainstream consensus algorithms( PoW and PoS ) are facing, which are high energy consumption and resource utilization.
Proof of Elapsed Time( PoET ) prevents these two problems by following a lottery-like system. Each node in the network is required to wait for a randomly chosen time period. The one who completes the waiting time, wins the new block. Each node in the network generates a random time for which it waits and goes to standby/sleep mode. The node to wake up first commits a new block to the blockchain and broadcasts the information to the whole network.
Mining cryptocurrencies that have PoET as their consensus algorithm must be very easy, right? Yes, but sadly their isn't any cryptocurrency till the date that uses this consensus algorithm yet. So, then where is it used? It is primarily used in Hyperledger Sawtooth.
What is Hyperledger Sawtooth? Hyperledger Sawtooth is a distributed ledger, which is kinda similar to Blockchain or it might be safe to say, private blockchain. Hyperledger Sawtooth designed for enterprise uses like supply-chain, logistics, accounting, etc.
Practical Byzantine Fault Tolerance(pBFT)
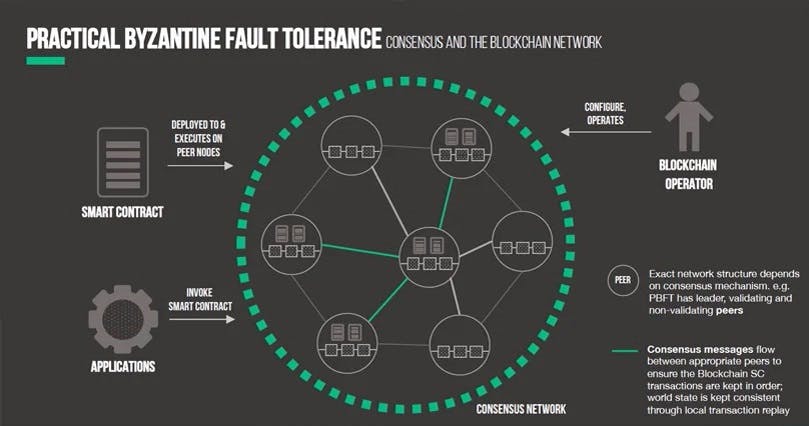
This is the most confused Consensus Algorithm in Blockchain for now to learn. I've tried to make it as simple as i could.
pBFT is a feature or we can say a Consensus Algorithm, of which main purpose is to work efficiently in case of certain cases node failures in the network. It improve the robustness and performance by directing peer-to-peer messages with minimal latency. It safe-guards the system failures by employing collective decision making of both correct and faulty nodes, which aims to reduce the influence of faulty nodes. It is derived from Byzantine Generals' Problem. To this network, smart contracts are deployed and executed on peer nodes.
The Applications are then used to invoke the smart contracts. pBFT has leader nodes and secondary or backup nodes(validating and non-validating nodes).
pBFT consensus rounds are broken into 4 phases:
-The clients node sends a request to the leader nodes.
- The leader node broadcasts the request to all the secondary nodes.
- The leader and secondary nodes complete the request and send back the reply to the client node.
- The request is served successfully when the client receives 'm+1' replies from all the different nodes in the network with the same result, where m = maximum number of faulty nodes allowed.
The consensus messages flow between the appropriate peers to ensure that the Blockchain Smart Contract transactions are kept in order.
There are two types of Byzantine Failures, the first one is Fall-Stop( in which the node fails to operate ) and the second one is arbitrary-node failures which include failure to return a result, respond with an incorrect result, respond with a deliberately misleading result, or respond with a different result to different parts of the system/network.
As every other consensus algorithm feature, pBFT has it's own PROs and CONs.
PROs
- ENERGY EFFICIENCY: pBFT can achieve consensus without complex mathematical computations like PoW. Zilliqa is a blockchain network using pBFT with a PoW-llike complex computations round for every 100th block added to the chain.
-TRANSACTION FINALITY: The transactions are not required multiple confirmations after they have been finailized and agreed upon like in case of PoW where all the nodes verifies all the transactions individually to add the new block to the blockchain, confirmations can takes 10-60 minutes depending on how many nodes confirm the new block.
- LOW REWARD VARIANCE: Every node take a part in responding to the request by the client node, so, every nodes is incentivized leading to low variance in rewarding the nodes that help in the process of decision making
CONs
pBFT works efficiently when the number of nodes in the distributed network is low due to the high communication vulnerability that increases exponentially with every extra node added in the distributed network.
SYBIL ATTACKS: pBFT is likely to be harmed by Sybil Attacks, where one party controls many indentities.
pBFT has scalability issues too so it is always used in combinations with other mechanisms.
Distributed Ledger
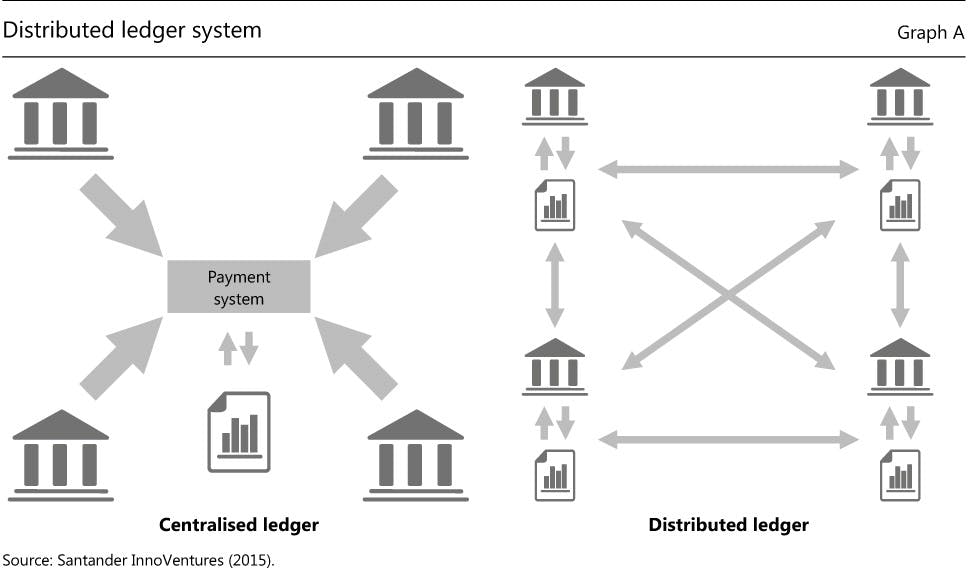 Distributed Ledger is where all of the transactions on the network are recorded.
Distributed Ledger is where all of the transactions on the network are recorded.
Where are the Transactions Recorded in Blockchain?
All the transactions taken place in a Blockchain Network are stored on a 'Distributed Ledger'.
By definition, A Distributed Ledger can be defined as a consensus of a synchronized and shared data in a digital format which is replicated to all the nodes in the network so we can say it is geographically spread across the globe.
It is distributed so there is no Central Storage of Data. This distributed nature of such ledgers are the reason of it being immutable. Even if a hacker tries to hack a single node and manipulate the data in the ledger, it'll be considered as faulty or byzantine node because the true data will be present on many other non-faulty nodes.
If you found this article useful:
- Follow ME
- Like it,
- BOOKMARK IT.
Quote of the day ~ Overthinking is the biggest cause of unhappiness
fin
